VPN
In order to connect your various locations with each other or to integrate your dedicated server into a central company network, the use of a virtual private network is a good idea. An encrypted connection - a so-called tunnel - is established between the end devices of the remote stations via an untrustworthy network. All network packets that are now forwarded to the respective network segment of the opposite end are protected against being read by third parties by means of encryption. When entering at the other end of the tunnel, the packet is decrypted again and forwarded to the local network.
A properly configured Virtual Private Network is based on three key points:
- Authentication
- Confidentiality with encryption
- Integrity with checksums
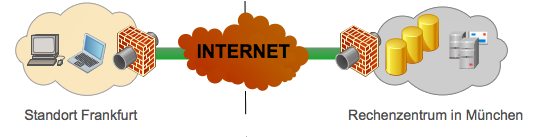
We realize these points and your requirements for a VPN with solutions based on the IP security (IPSEC) and OpenVPN (SSL/TLS-VPN) standards. A configuration with PPTP is also possible. This makes it possible, among other things, to set up the following business solutions:
- Site 2 Site - Connections (Network A - Network B)
- Roadwarrior (home users, sales, travelers) with password verification against backends (e.g. LDAP/AD)
- GRE-Tunnel, also with OSPF
In the case of connections between different company locations, the use of Metro Ethernet solutions is also possible in addition to the use of the technology already in use (VDSL, dial-up connections, E1, E2, E3...). Here, with our partners in the carrier sector, we can enable Ethernet via MPLS lines from and to various locations up to the data center.